Keylogger
Spyware - Activity-monitoring software program that give access to personal data
Disclaimer: This project was done under research and in a controlled environment, for educational purposes only.
What I managed to create in this project was a keylogger developed in Python and furthermore a way how this kind of spyware can be transmitted to other Windows devices without being detected by the up-to-date Windows Defender (30/12/2022).
I will also exemplify how this type of malware is shared with a bit of social engineering and no interface, hiding the processes responsible for the malware from the user.
From the moment the spyware is executed it is forever bound to this windows user, until it is detected and removed. From that point on, whenever the user's computer starts up, the spyware will always run as a hidden process.
For this project I used:
- Python
- Microsoft PowerShell
- Command Prompt
- VBScript scripting language
- JavaScript
- Html & Css
Full code source on my GitHub: https://github.com/OlegLeo/Remote_KeyLogger
These kinds of projects only serve to simulate and understand the cyber attacks that happen in the real world, for educational purposes only!
To create a local web server, just as an example I used XAMPP, there are many other tools that do the same.
Next to make the site quickly accessible outside my local network, I used NGROK, by typing the command "ngrok http 80". A link is generated that can be publicly shared, as shown in the video above.
Usually these types of attacks are shared via email, social media, etc.
The attackers create fake campaigns that try to convince people to believe them and download some kind of file to be executed containing some malicious script without the user knowing.
When accessing the link a file is created automatically on the client side computer (written in JavaScript).
Basically to avoid a direct download of an executable file from the web server, I order to create a file on the local computer on the client side and write the file with some malicious commands. This way there is less chance that the antivirus will detect it as a suspicious file.
The visual part of the web page is made in html and css that was created just to serve as an example. (index.html file, the complete code is in my github repository).
Of course, the attacker will always try to convince you that the file has to be executed, using social engineering techniques.
What the average user doesn't know is that at this stage any kind of malicious code can be running in subprocess.
Just for example I used a .vbs file, which can be executed natively by windows. It could be a word or excel document containing malicious macros, a .cmd file, .bat, .exe, etc.
Most of these executables are marked as suspicious by antivirus software, which causes the attackers to use ways to convince the person to believe that the file is trustworthy and disable some security measures of windows.
Using the VBScript scripting language, with a .vbs executable file I gain access to the terminal (powershell) of the victim's computer, I first ask to open a web-page with a voucher code and then while hiding the runtime interface from the user:
-Transfer the .zip document with python to the path "C:\Temp"
-Extract the folder
-Transfer the PIP
-Install the dependencies of some necessary modules
-Download the keylogger script .py to the same path
-Finally run the keylogger
(full commented and easy to understand script inside "script.txt" file)
To make sure that whenever the computer turns on and starts the keylogger .py script, I create and write a file in the path "%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup" to serve as a trigger to call the execution of keyloggerscript.py.
For testing purposes I created an email sender function inside keyloggerscript.py that makes everything that was pressed on the keyboard be sent every 20 seconds, as we can see in the video above.
keyloggerscript.py also has the possibility to send a .txt file, for example, which will save everything that was pressed on the keyboard.
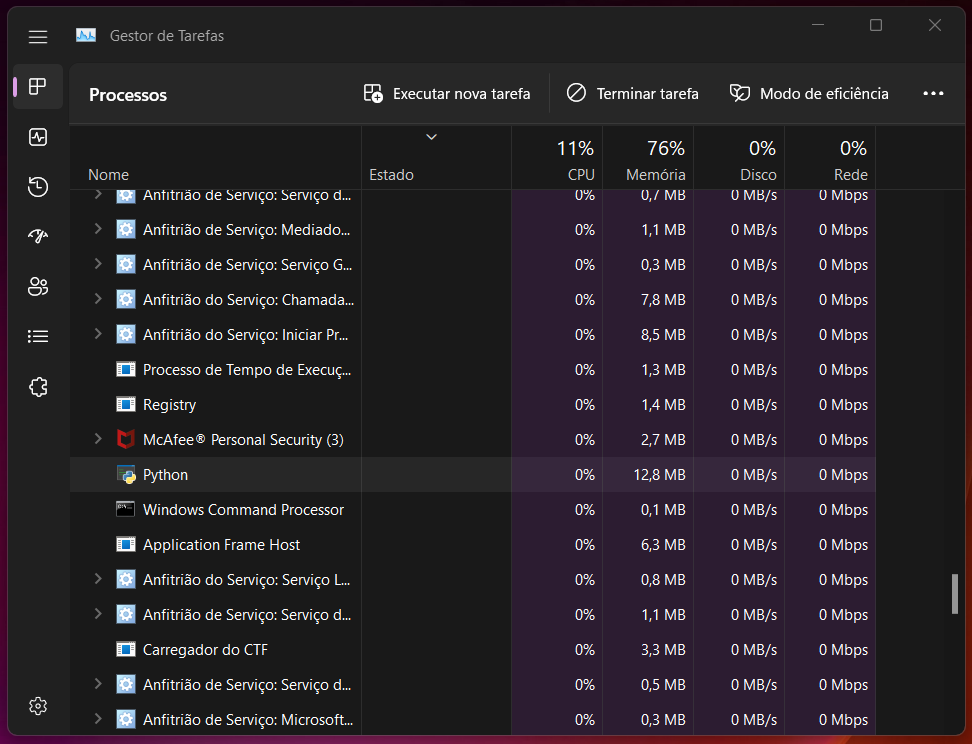
As we can see, when we open the Task Manager, we can find Python running as one of the processes, once again remembering that it runs without a user interface.
Conclusion: Why Python?
I discovered that this way can be considered a form of Windows vulnerability, because when downloading Python on the victim's computer, we don't need to officially install it and ask for administrator authorization, basically what we do is just transfer the files from an official website, Windows Defender does not detect it as strange behavior. And to be honest I think Python is an amazing programming language and easy to work with.
Full code source on my GitHub: https://github.com/OlegLeo/Remote_KeyLogger