Ransomware
Malicious Script - Encryption of files
I have always been curious to understand technically how a ransomware attack works.
Once the script is executed, all folders and subfolders are scrolled through and the files are encrypted.
In this example I used just for testing the directory called "test" with some subfolders containing other files. You can do exactly the same for example on the local disk computer C:\.
For this project I used:
- Python
- Microsoft PowerShell
- Command Prompt
Full code source on my GitHub: https://github.com/OlegLeo/Ransomware_Atack_Simulation/blob/main/enc_test.py
These kinds of projects only serve to simulate and understand the cyber attacks that happen in the real world, for educational purposes only!
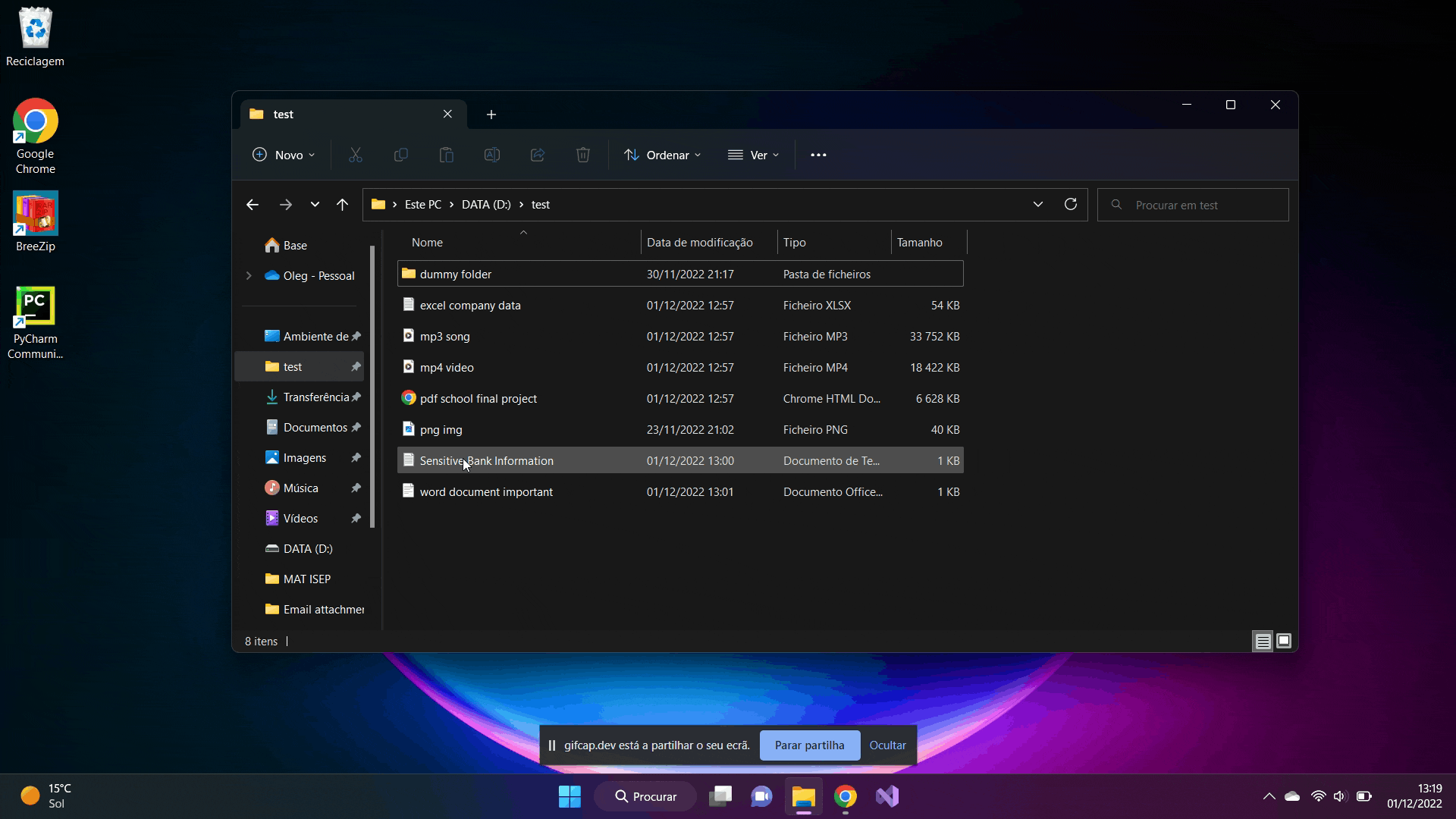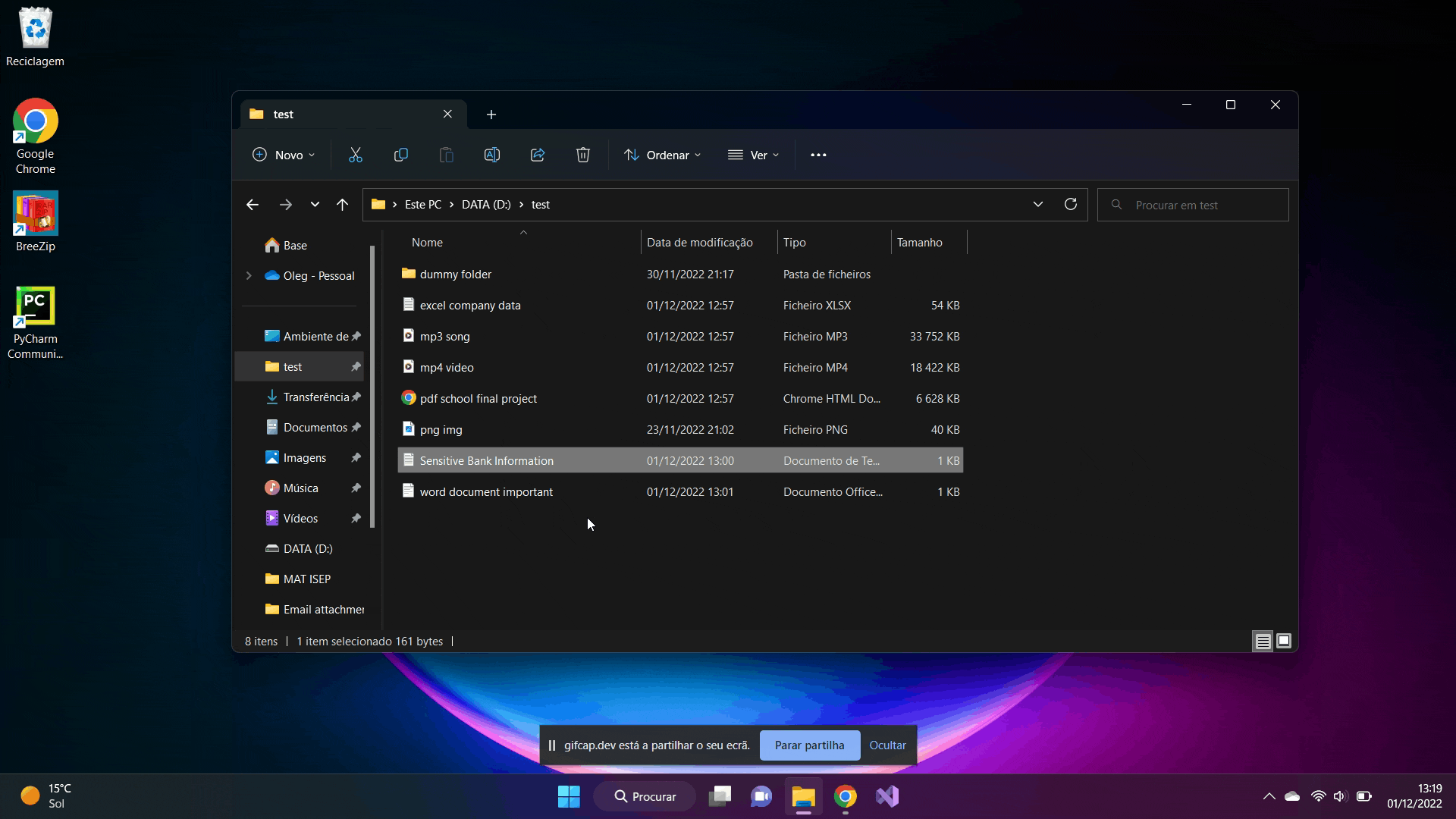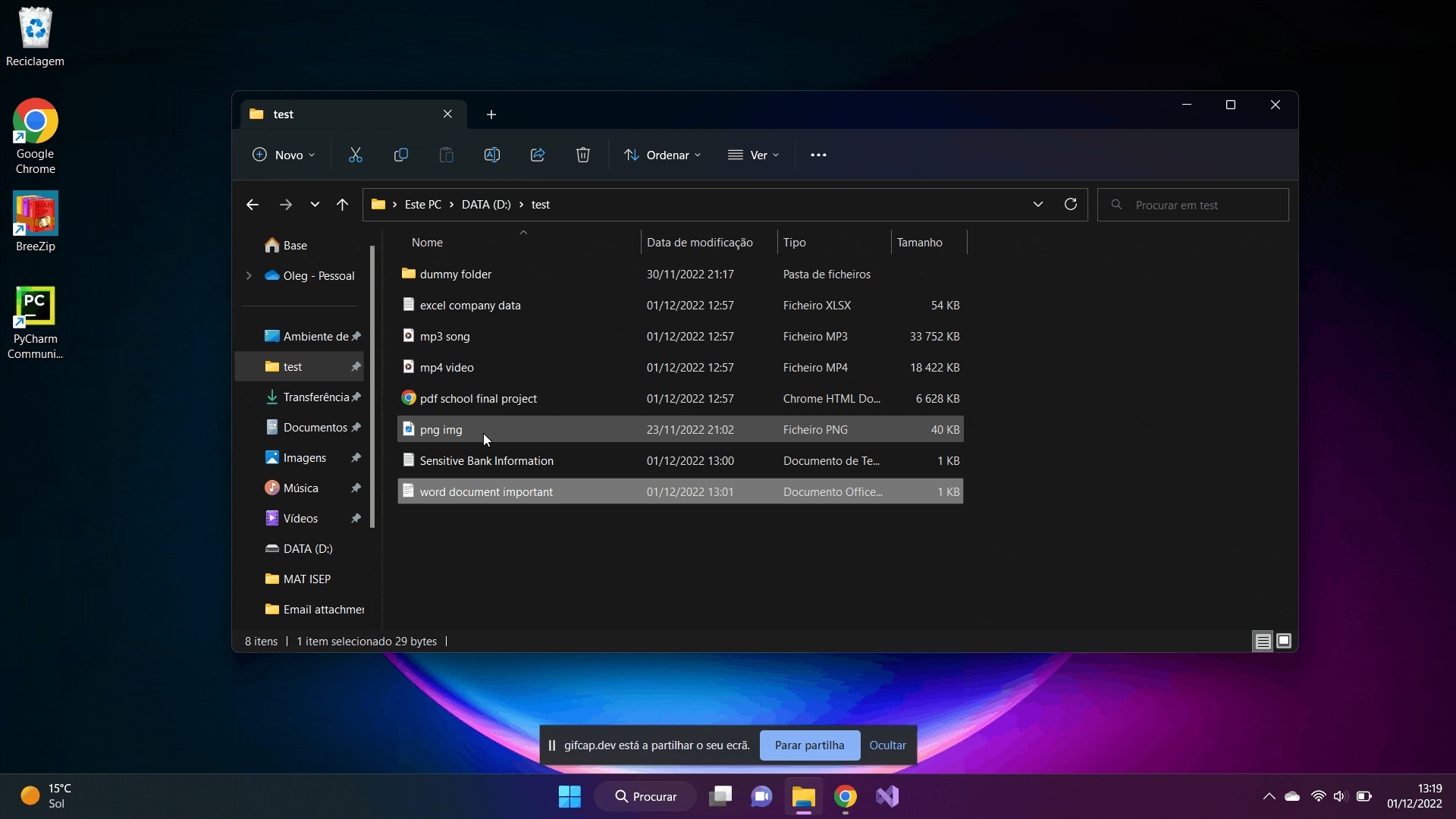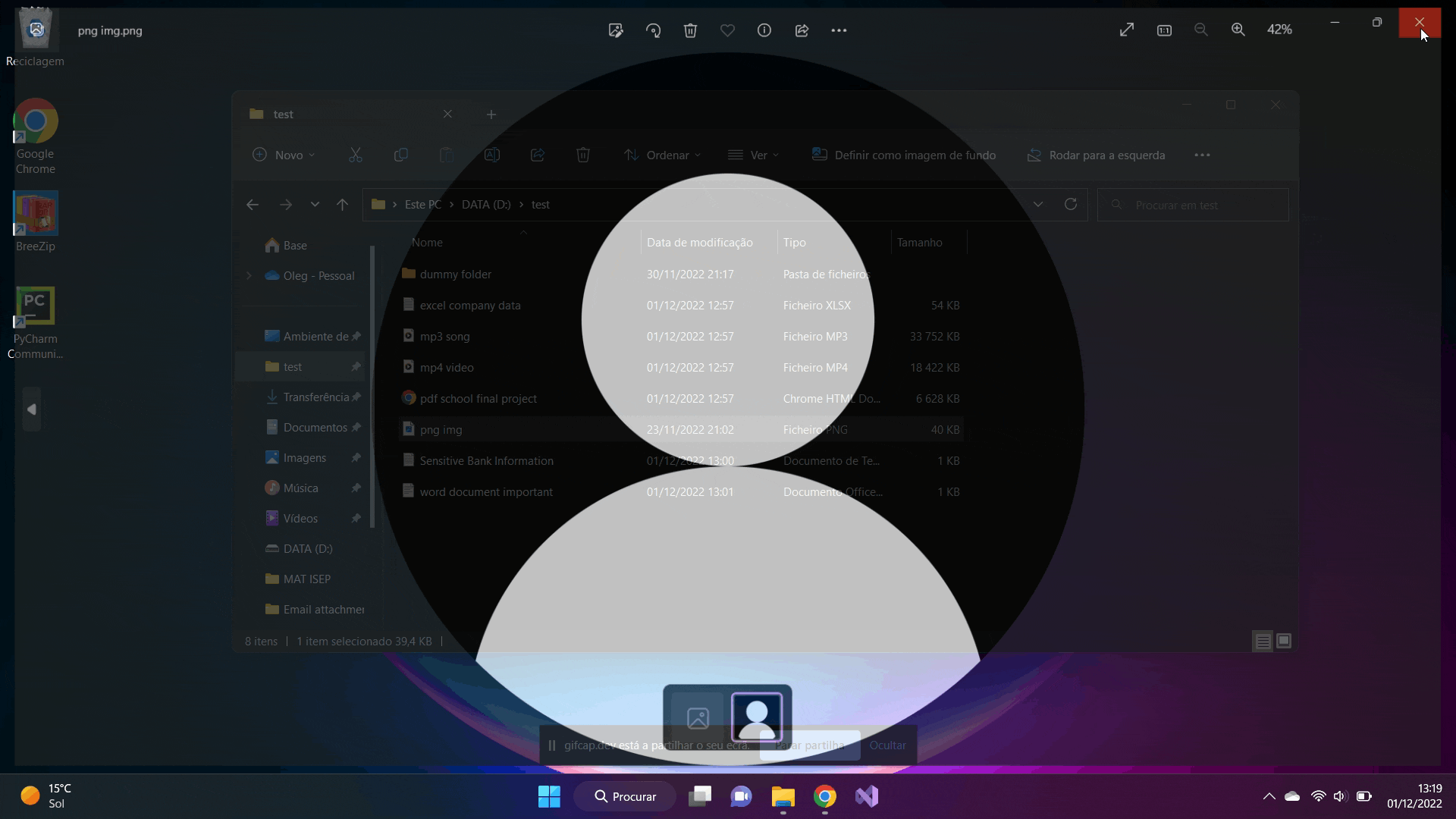
This directory contains some files of various types that are most commonly used by the average Windows user.
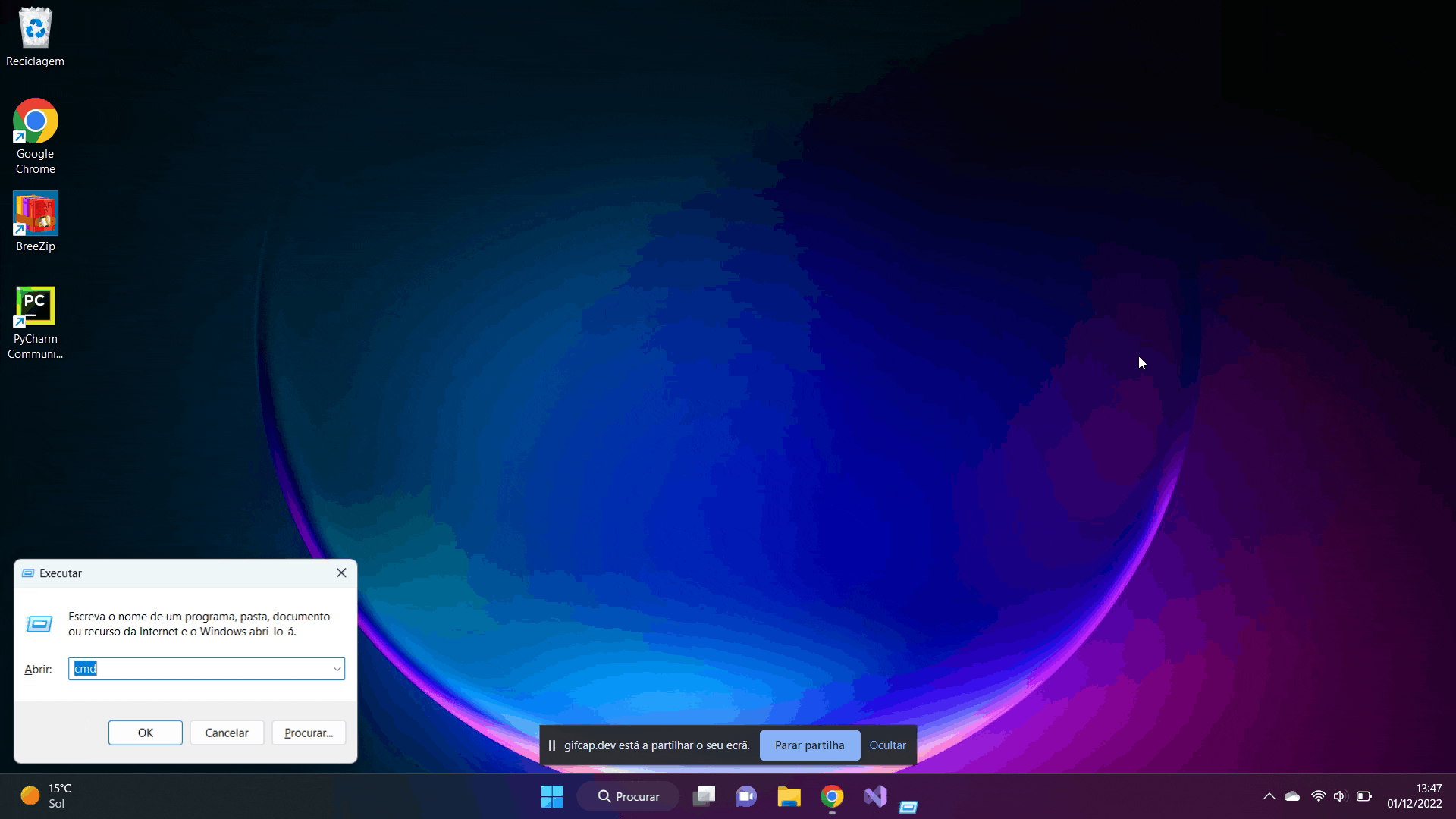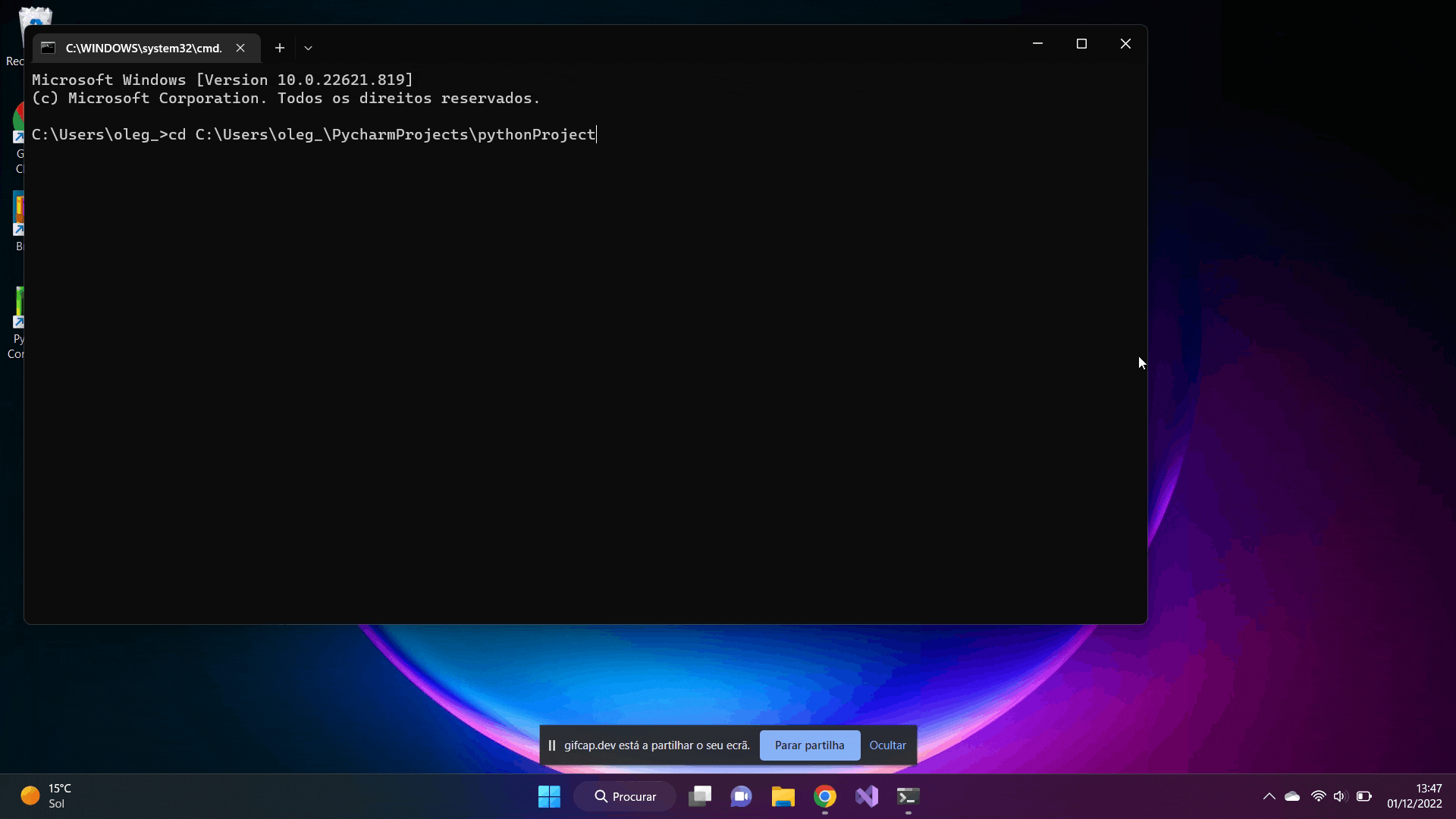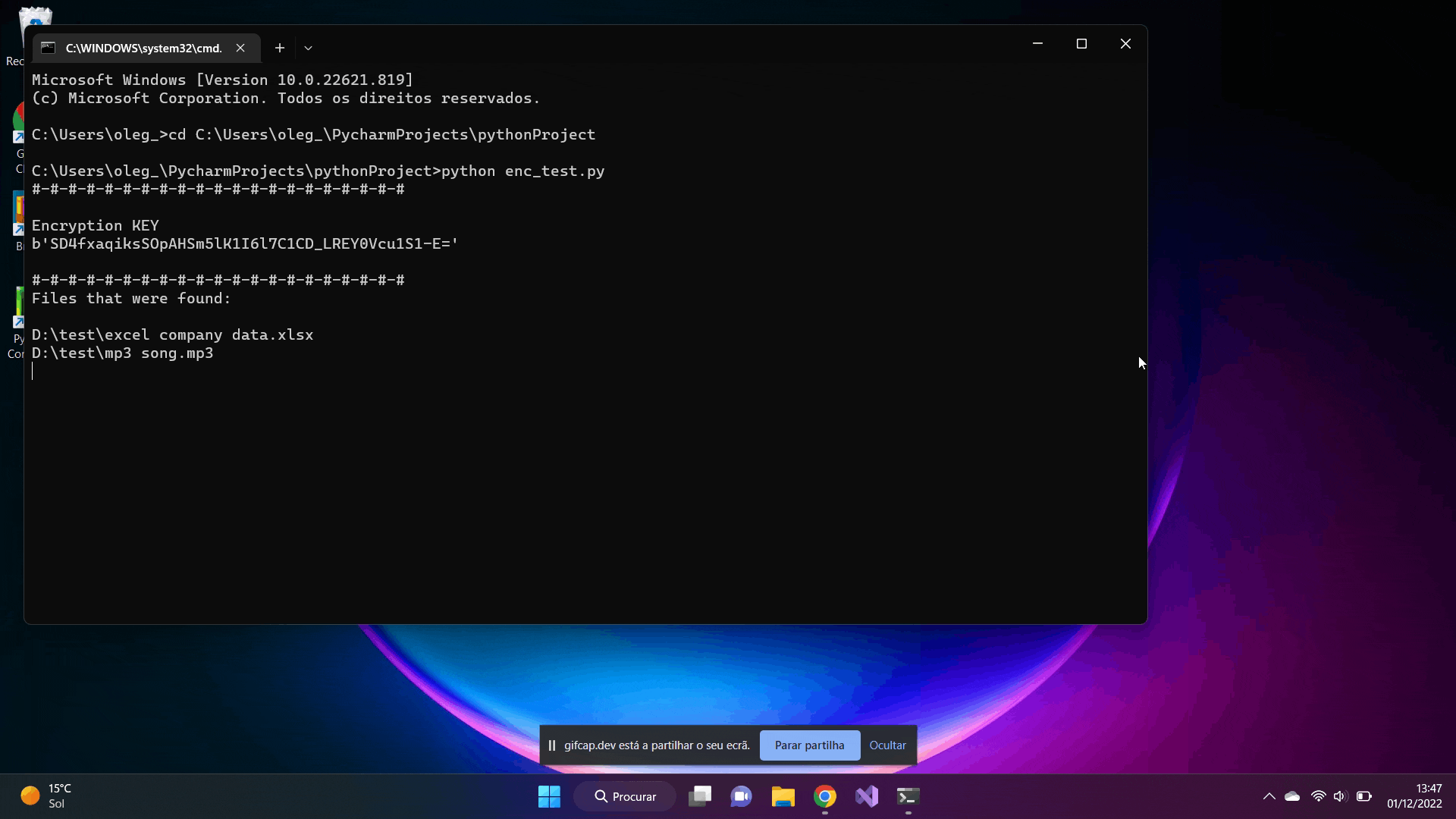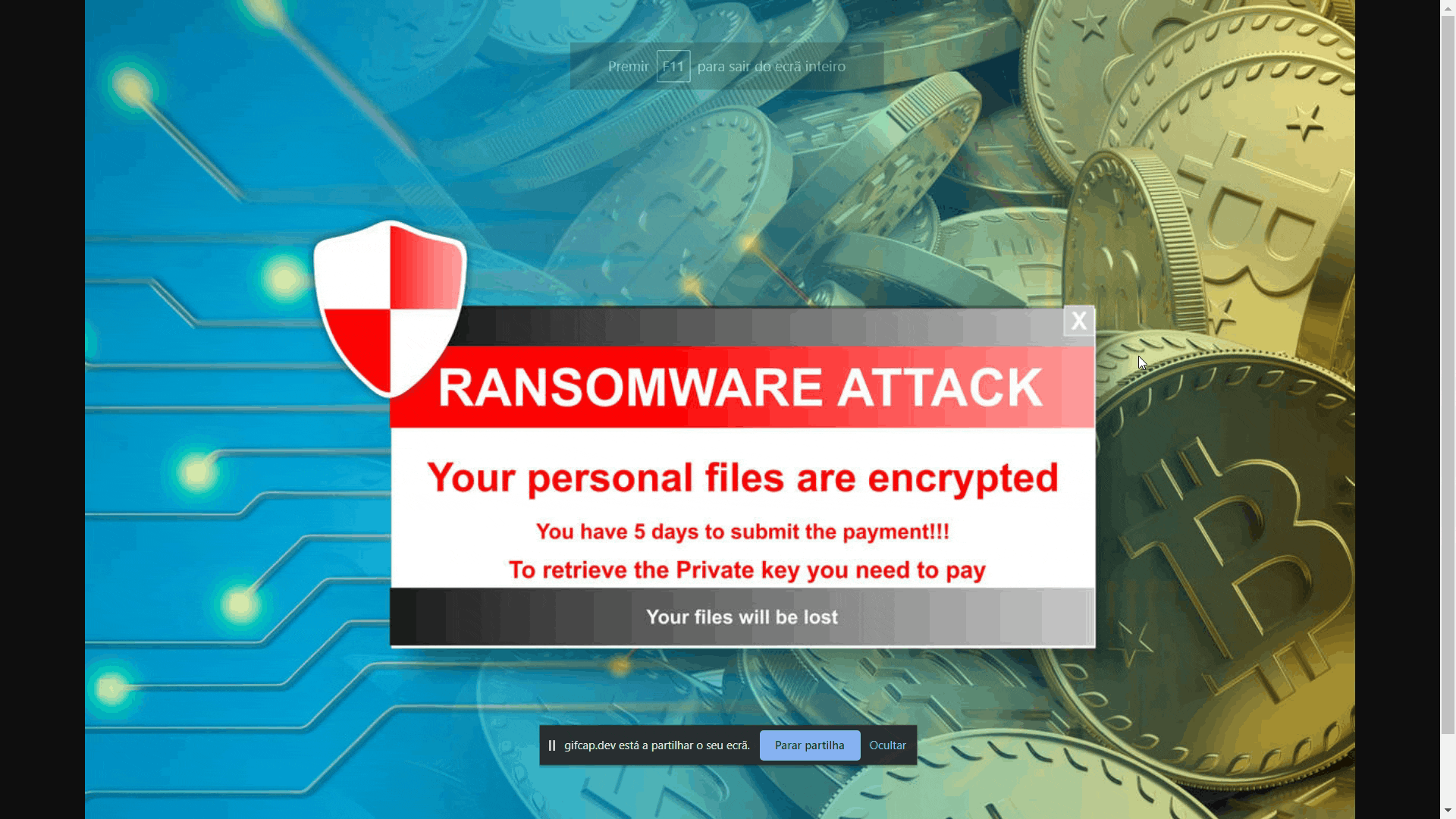
What we are doing here, we simply start the python script from the command line. At the top appears the generated key for encrypting the files which is used to decrypt the files. All the subfolders within the directory are scrolled through and all the files I defined in the code (e.g. .png, .mp3, .mp3, .txt , etc) are encrypted. It is possible to add as many file types as we want. And of course, you can't miss that classic pop-up warning that the files have been encrypted. I just did it for fun.
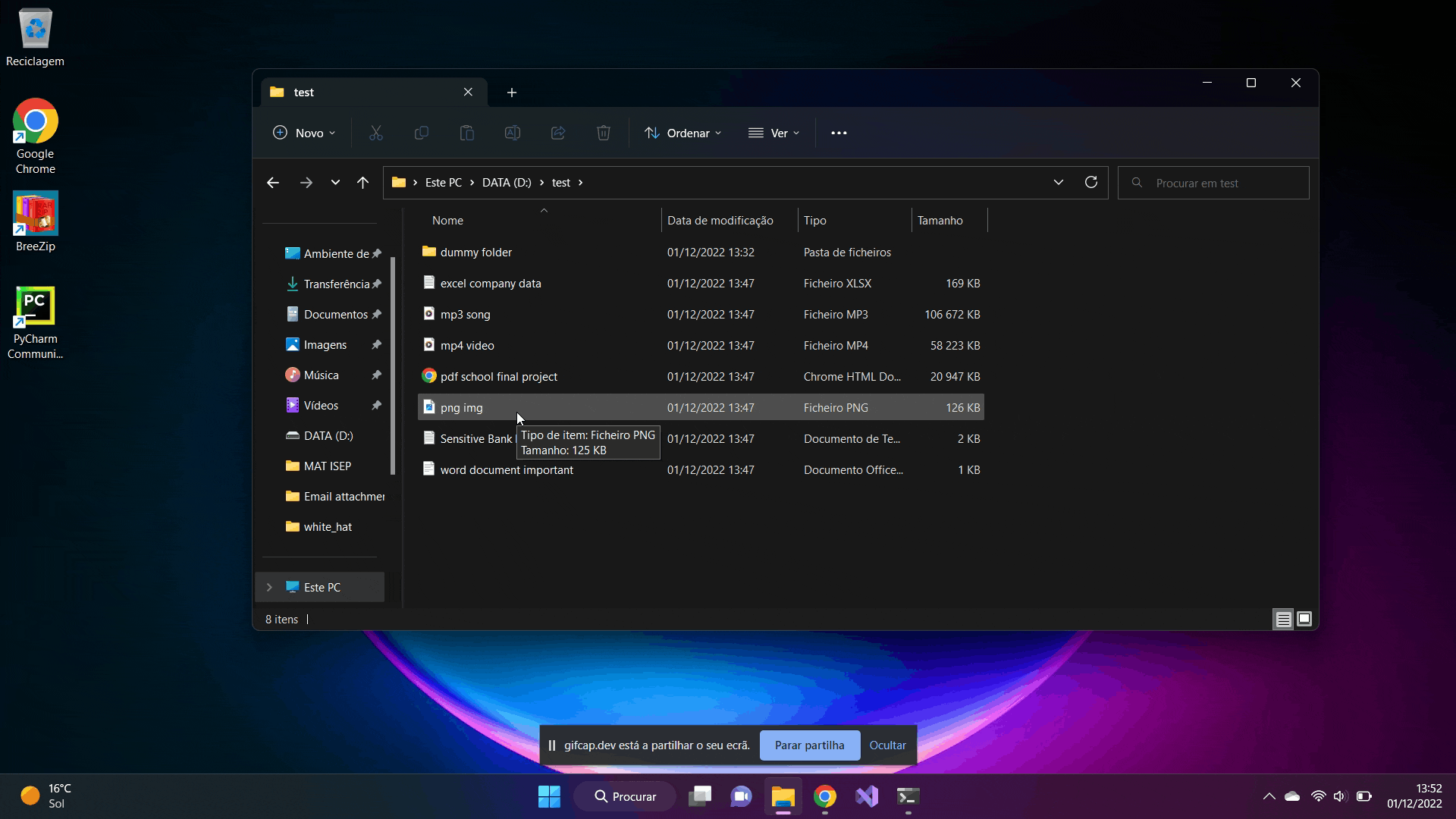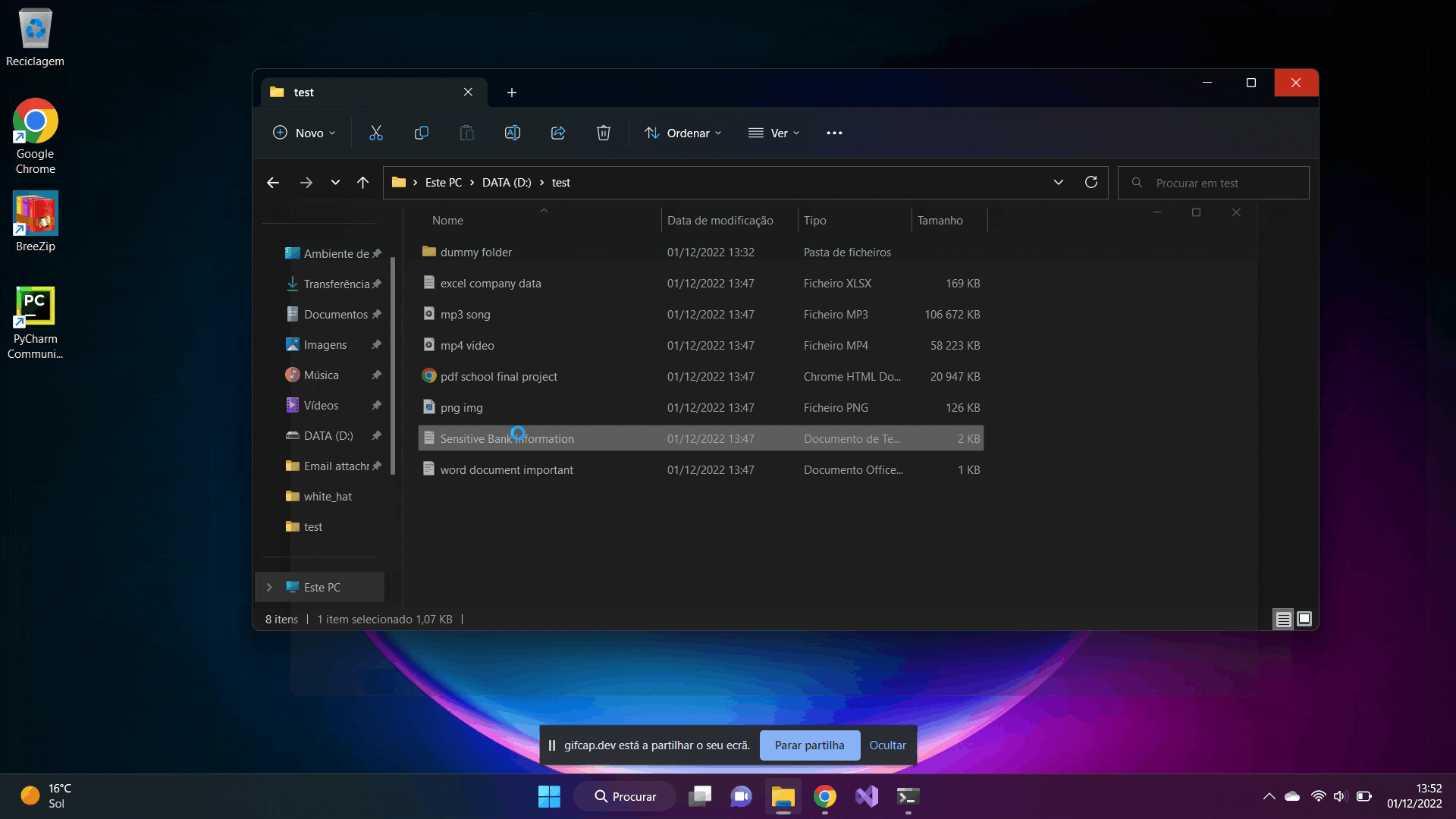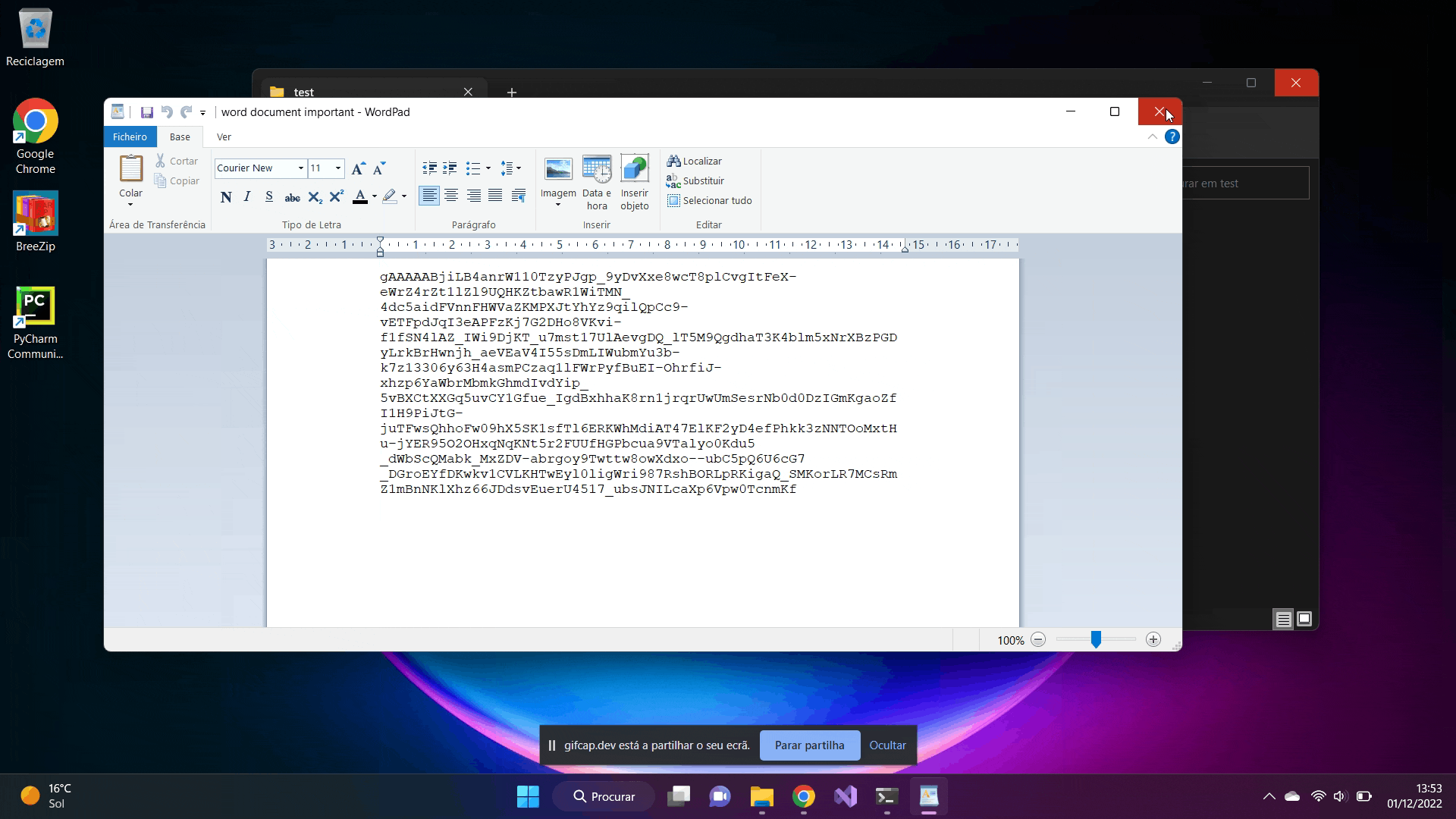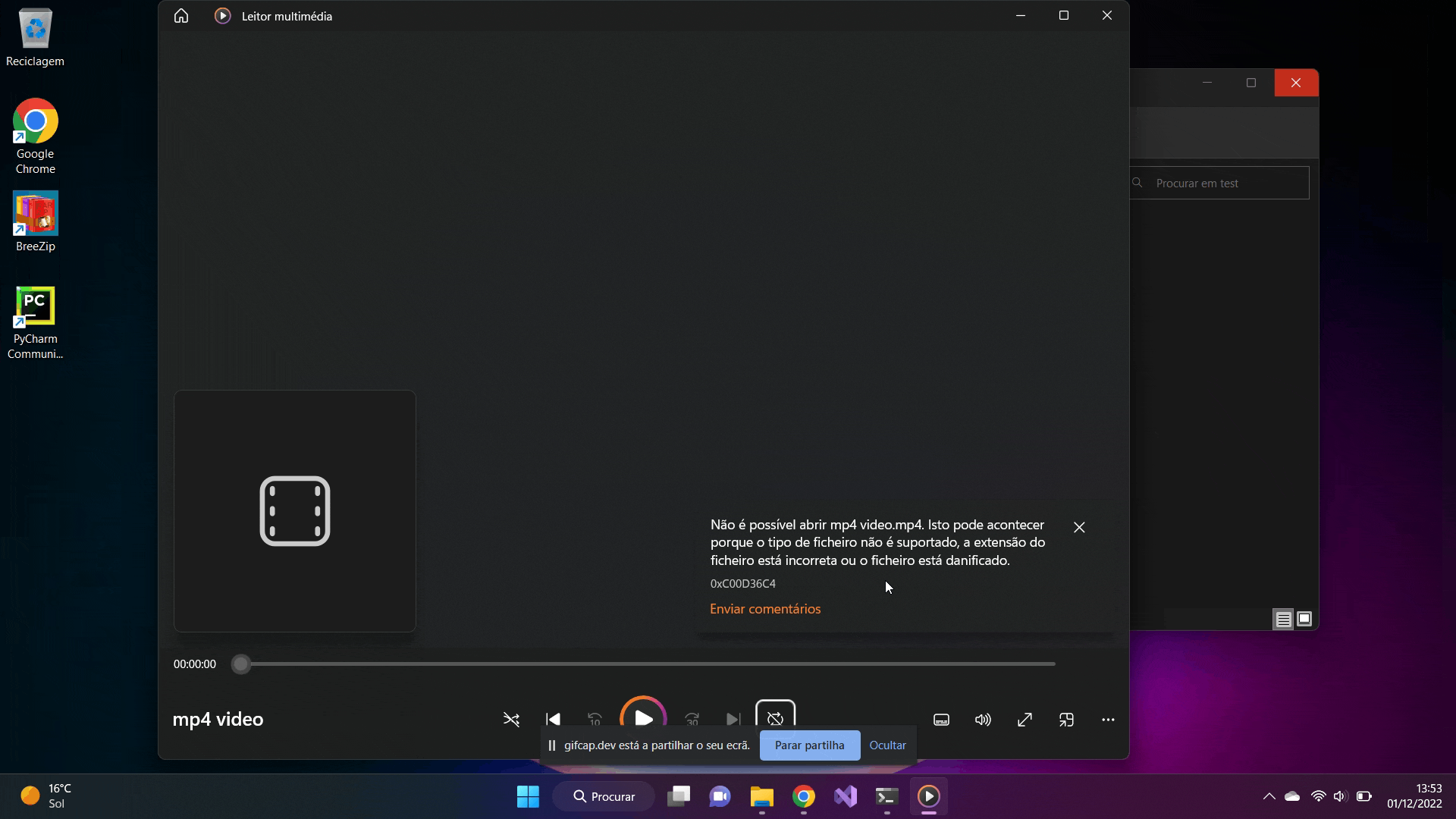
Finally we can see that all files have been successfully encrypted and cannot be accessed or read by the user. It is only possible to have them operational if they are decrypted.
As a reminder, all the code is on my github, commented out and easy to understand.
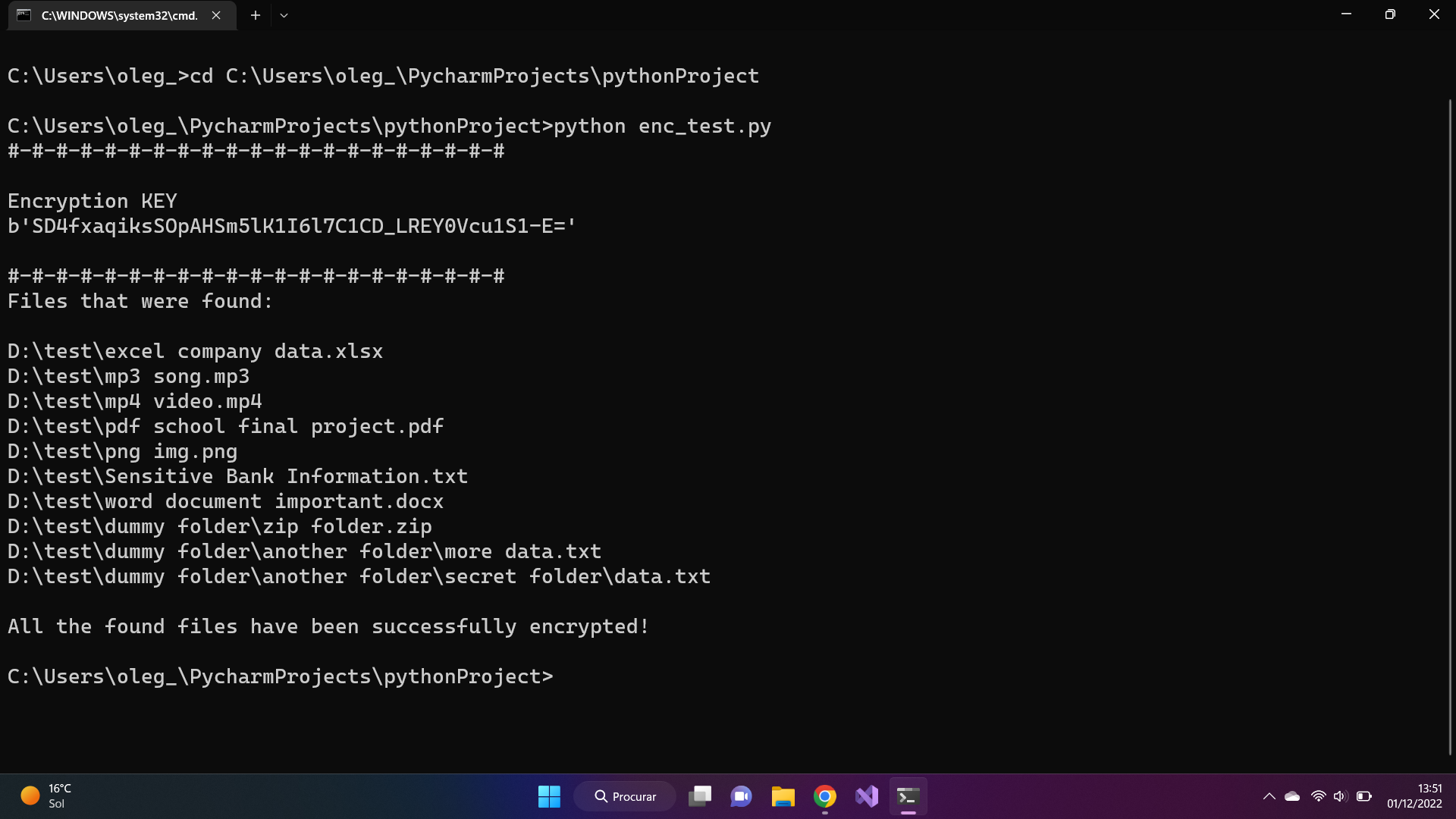
I also leave the image of the script output.